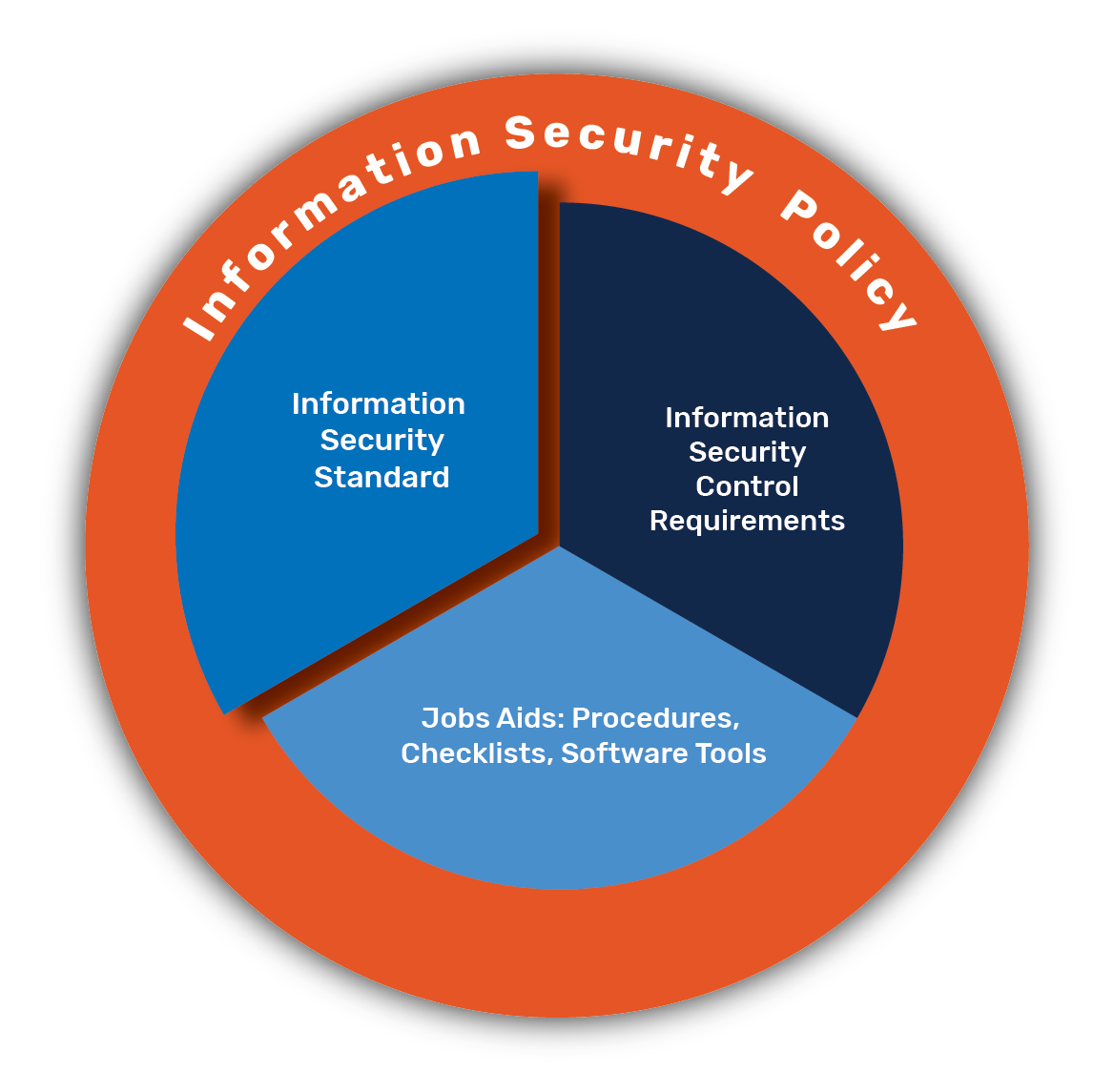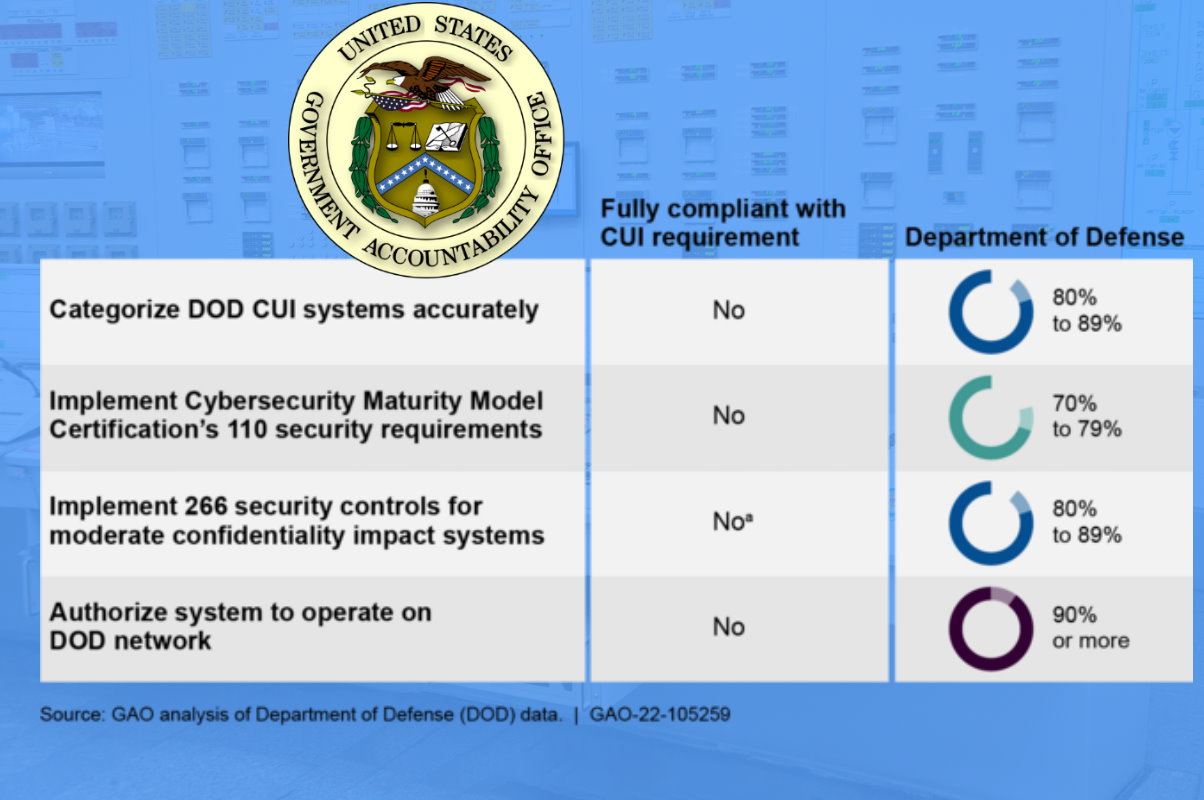
US GAO reports that DOD has partially implemented selected cybersecurity requirements for CUI systems - Industrial Cyber
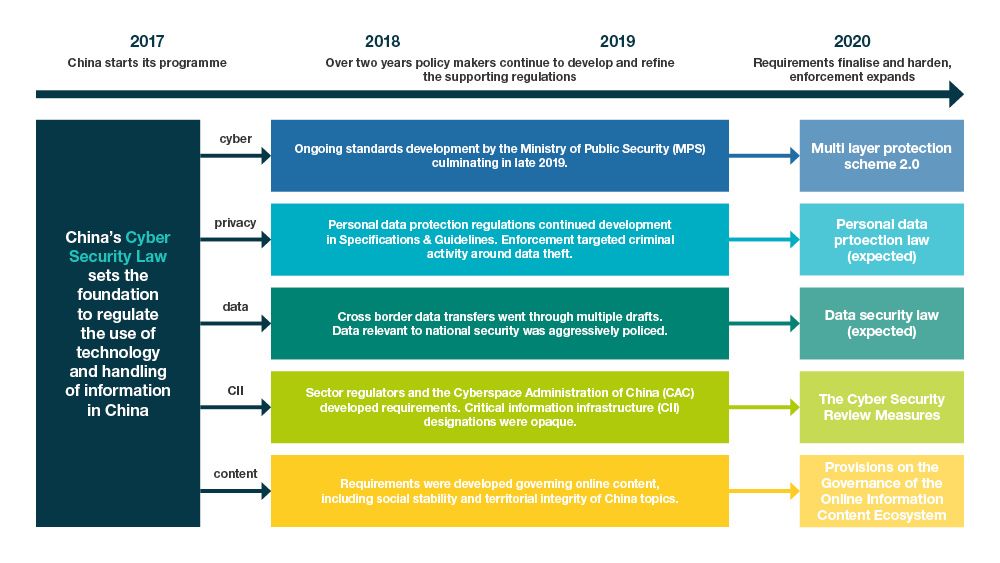
Enforcement of China's Multi-Level Protection Scheme: The rapid roll-out of cyber security compliance
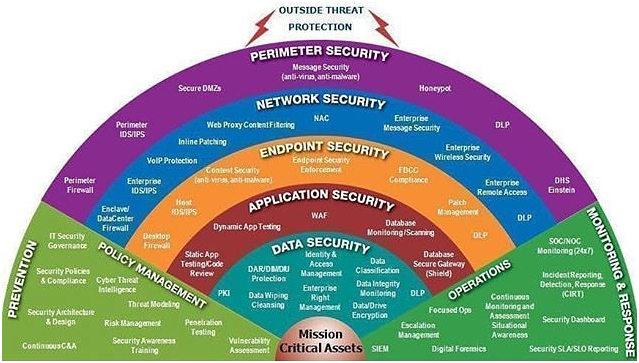
New York Cybersecurity Requirements for Financial Services Companies (NY-CRFSC) | by Golden Data Law | Golden Data | Medium